Identity And Access Management Market Report
Published Date: 31 January 2026 | Report Code: identity-and-access-management
Identity And Access Management Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Identity and Access Management (IAM) market, covering critical insights into market size, trends, segmentation, and regional dynamics from 2023 to 2033.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
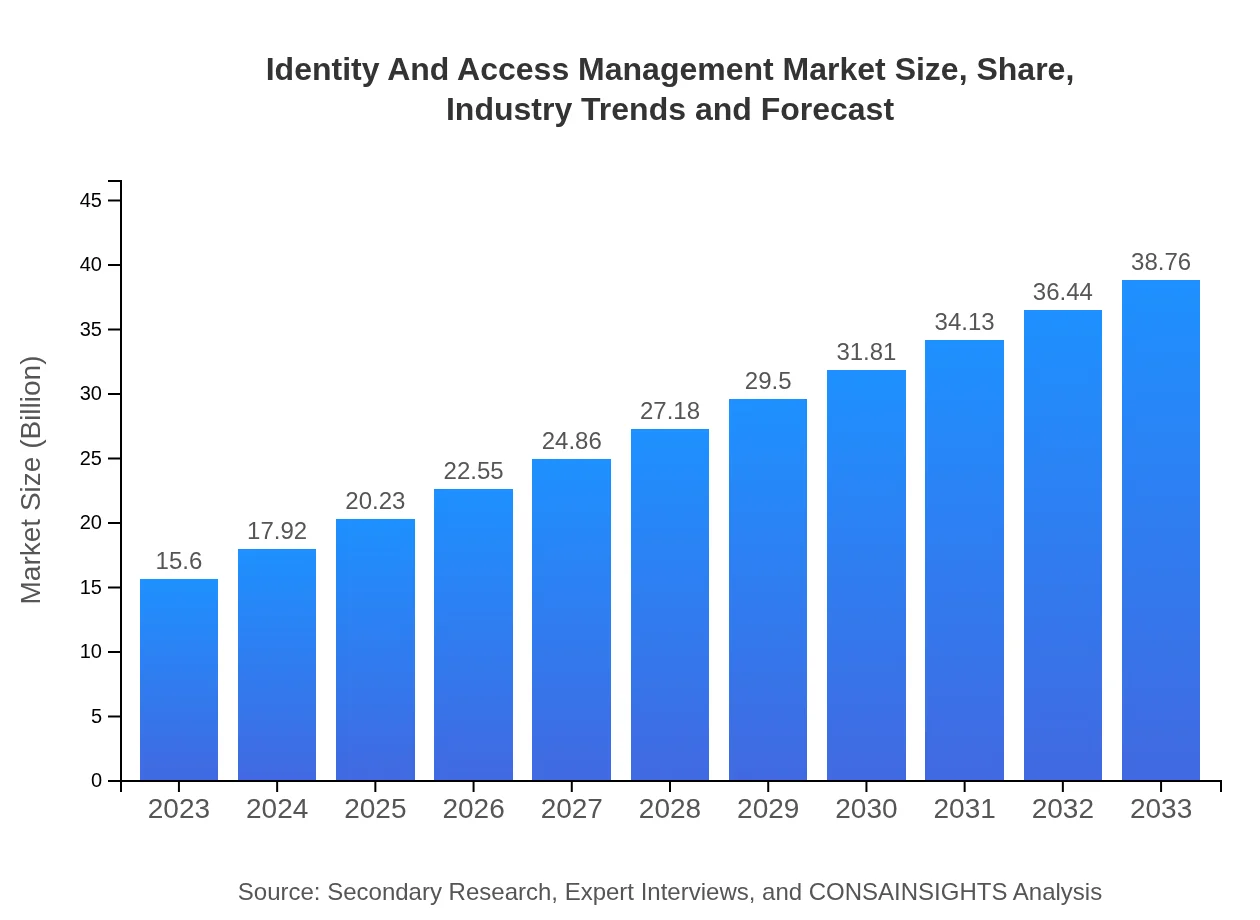
| 2023 Market Size | $15.60 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $38.76 Billion |
| Top Companies | IBM Corporation, Okta, Inc., Microsoft Corporation, SailPoint Technologies, Ping Identity Corporation |
| Last Modified Date | 31 January 2026 |
Identity And Access Management Market Overview
Customize Identity And Access Management Market Report market research report
- ✔ Get in-depth analysis of Identity And Access Management market size, growth, and forecasts.
- ✔ Understand Identity And Access Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Identity And Access Management
What is the Market Size & CAGR of Identity And Access Management market in 2023 and 2033?
Identity And Access Management Industry Analysis
Identity And Access Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Identity And Access Management Market Analysis Report by Region
Europe Identity And Access Management Market Report:
Europe's IAM market is anticipated to escalate from $4.76 billion in 2023 to $11.82 billion by 2033, influenced by stringent data privacy regulations such as GDPR and a growing emphasis on securing digital identities.Asia Pacific Identity And Access Management Market Report:
The Asia Pacific region is poised for significant growth, increasing from a market size of $2.75 billion in 2023 to approximately $6.82 billion by 2033, driven by widespread digitalization and heightened awareness of cybersecurity needs.North America Identity And Access Management Market Report:
North America remains the largest IAM market, projected to grow from $5.81 billion in 2023 to $14.43 billion by 2033. Factors bolstering this growth include early technology adoption, a strong focus on compliance, and increasing cybersecurity budgets across enterprises.South America Identity And Access Management Market Report:
In South America, the IAM market is expected to expand from $0.64 billion in 2023 to about $1.60 billion in 2033. The growth in this region is facilitated by increased adoption of cloud technologies and the urgent need for secure identity management.Middle East & Africa Identity And Access Management Market Report:
The IAM market in the Middle East and Africa is forecasted to rise from $1.65 billion in 2023 to $4.09 billion by 2033. The demand for robust cybersecurity solutions is accelerating in this region due to increasing economic investments and digital initiatives.Tell us your focus area and get a customized research report.
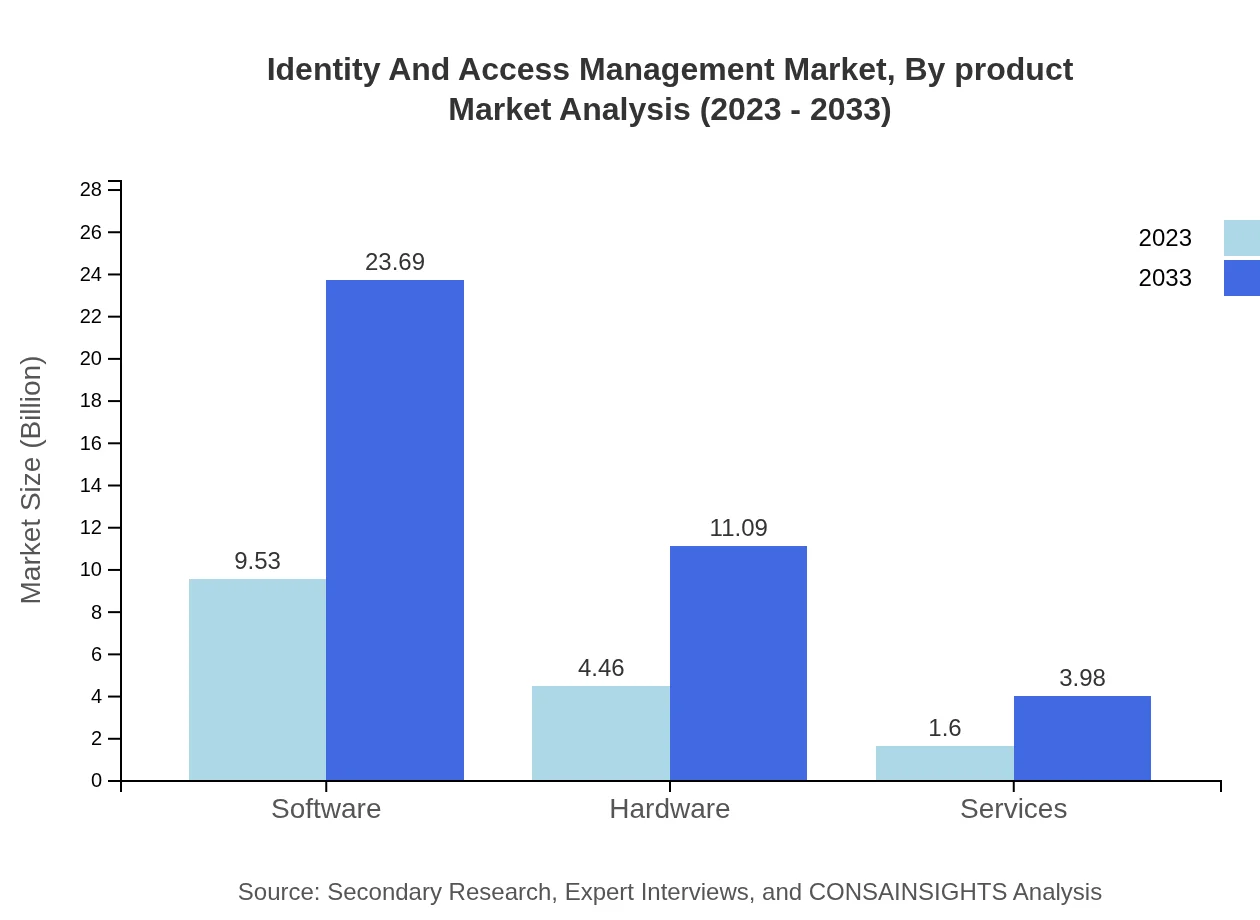
Identity And Access Management Market Analysis By Product
The IAM market, segmented by product type, reflects significant growth across software, hardware, and services. The software segment leads in market share, projected to grow from $9.53 billion in 2023 to $23.69 billion by 2033, accounting for approximately 61.11% share in both years. Hardware solutions and service offerings also showcase robust growth, indicating a diverse set of offerings supporting IAM.
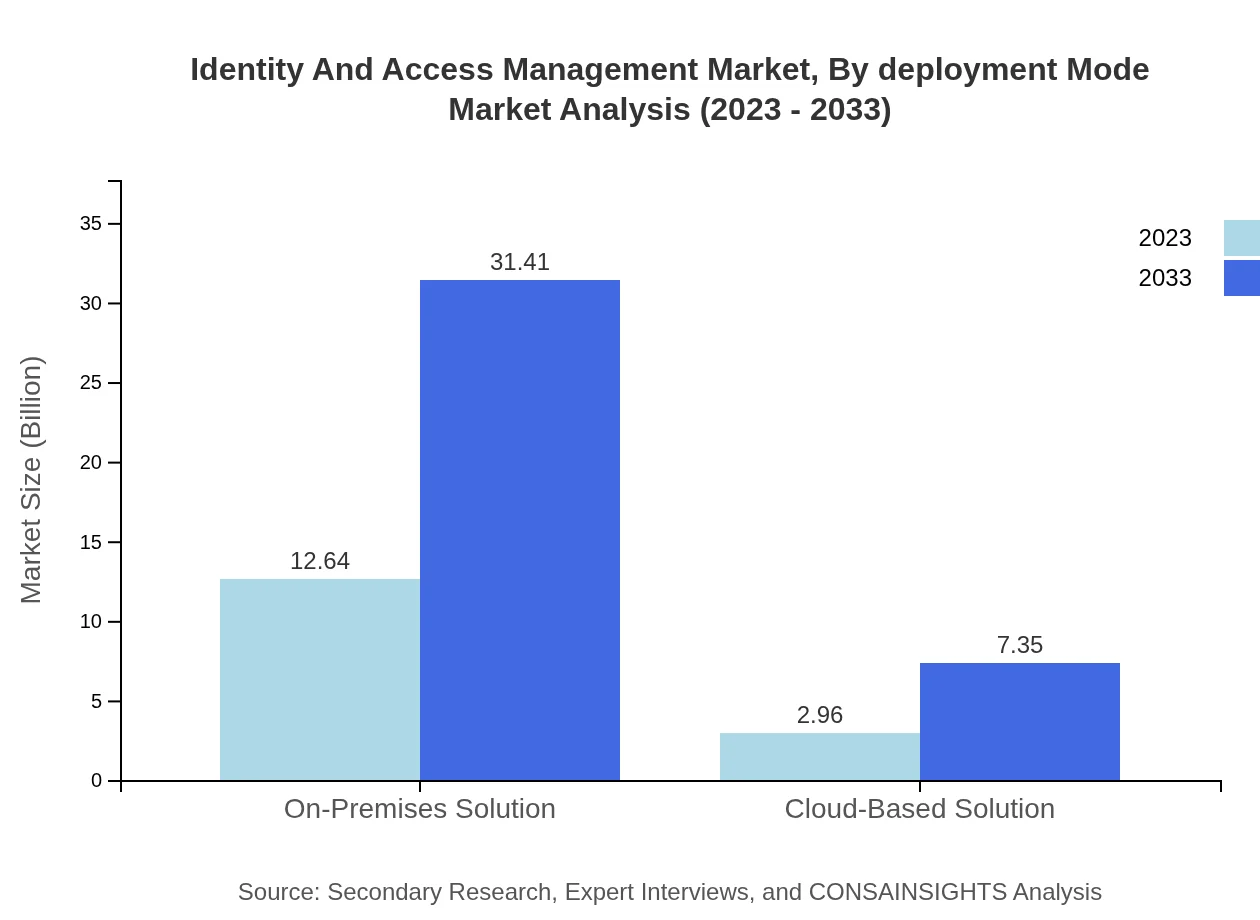
Identity And Access Management Market Analysis By Deployment Mode
Deployment modes in the IAM sector predominantly include on-premises and cloud-based solutions. On-premises solutions are expected to remain prevalent, growing from $12.64 billion to $31.41 billion by 2033, while cloud-based solutions show a growth from $2.96 billion to $7.35 billion, underlining a shift towards flexible, scalable identity management solutions.
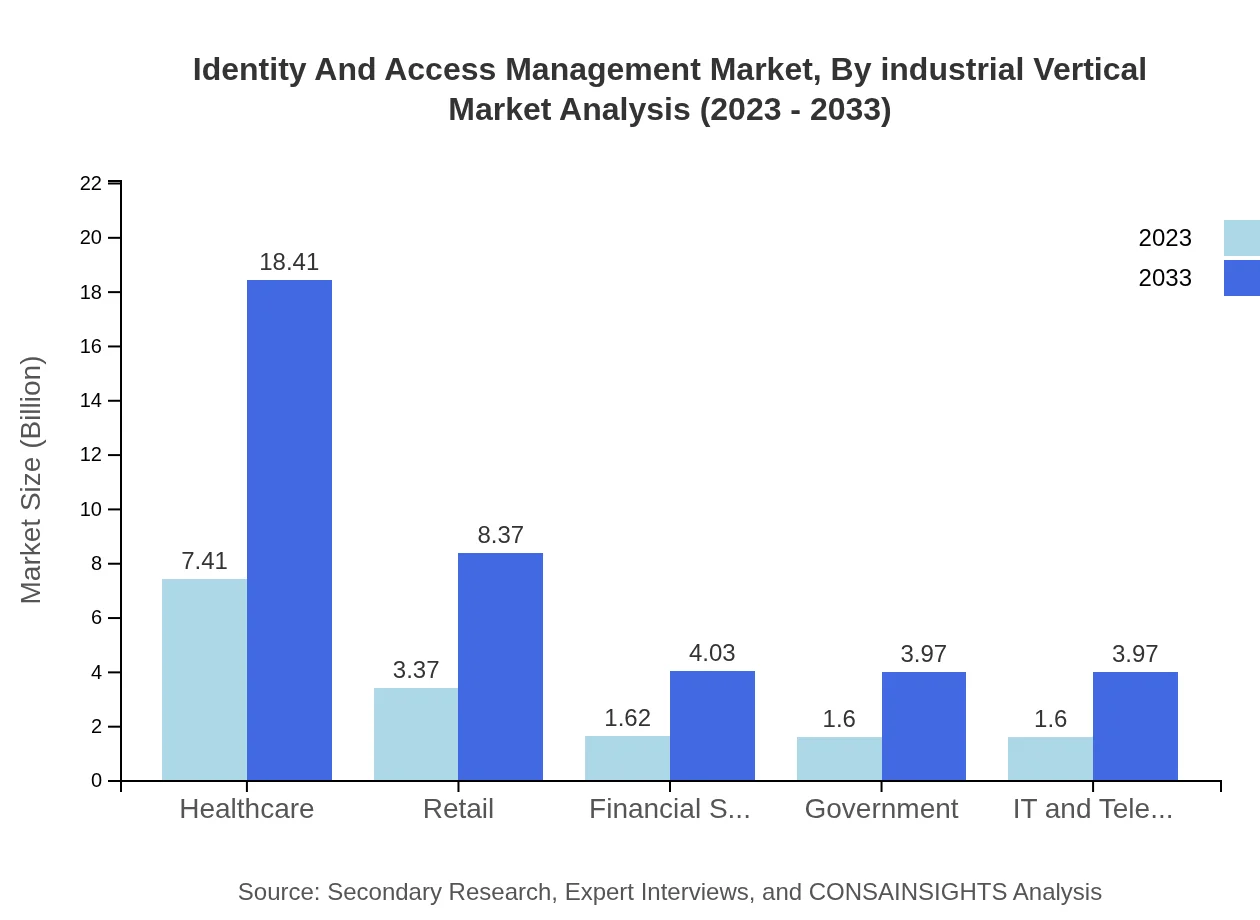
Identity And Access Management Market Analysis By Industrial Vertical
The IAM market finds substantial application across various industrial verticals such as healthcare, retail, financial services, government, and IT & telecom. Healthcare leads with a market size increase from $7.41 billion to $18.41 billion by 2033, indicating the critical need for secure handling of sensitive patient data.
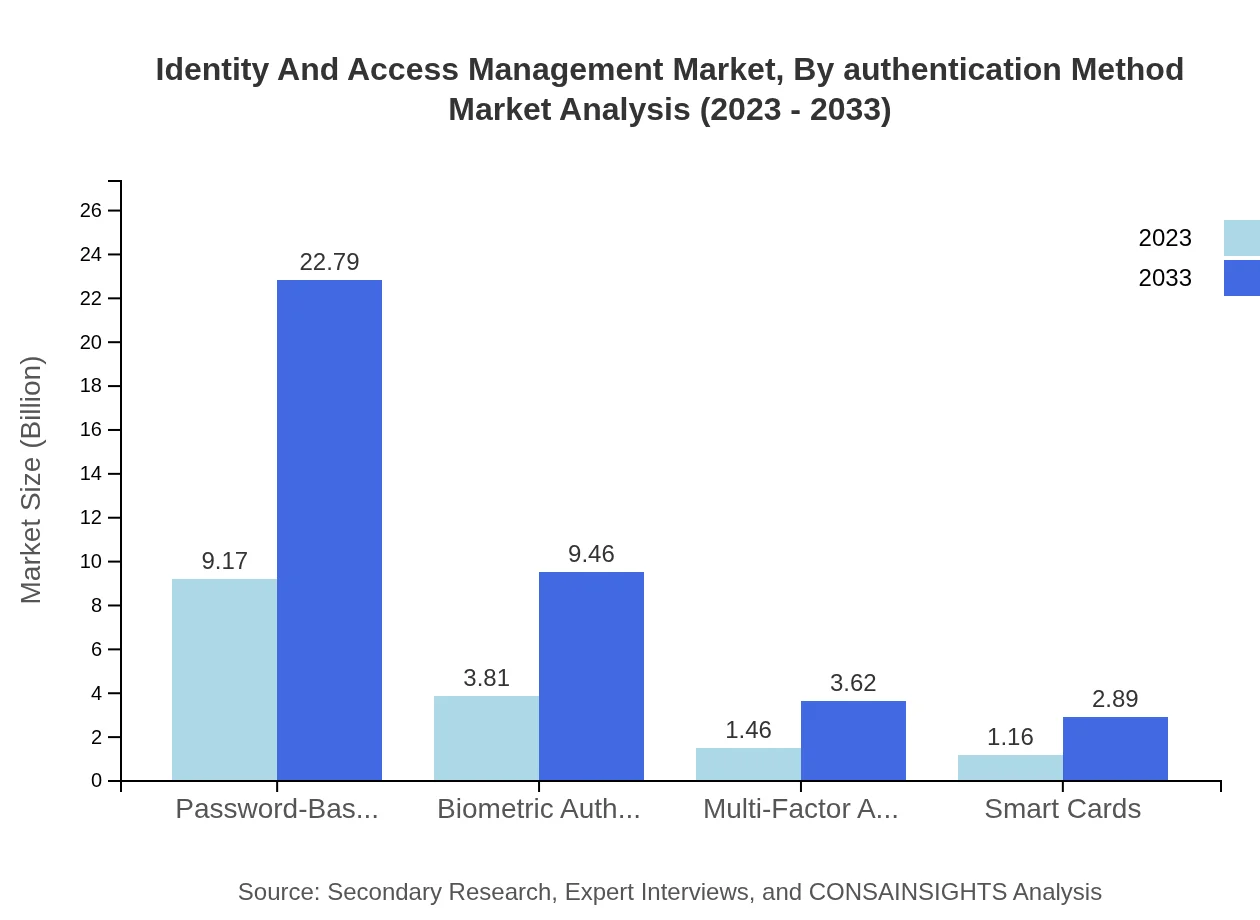
Identity And Access Management Market Analysis By Authentication Method
Authentication methods in the IAM space consist of password-based authentication, biometric authentication, multi-factor authentication, and smart cards. Password-based systems dominate the market, expected to grow from $9.17 billion to $22.79 billion by 2033, while biometric solutions are also on the rise as security needs escalate.
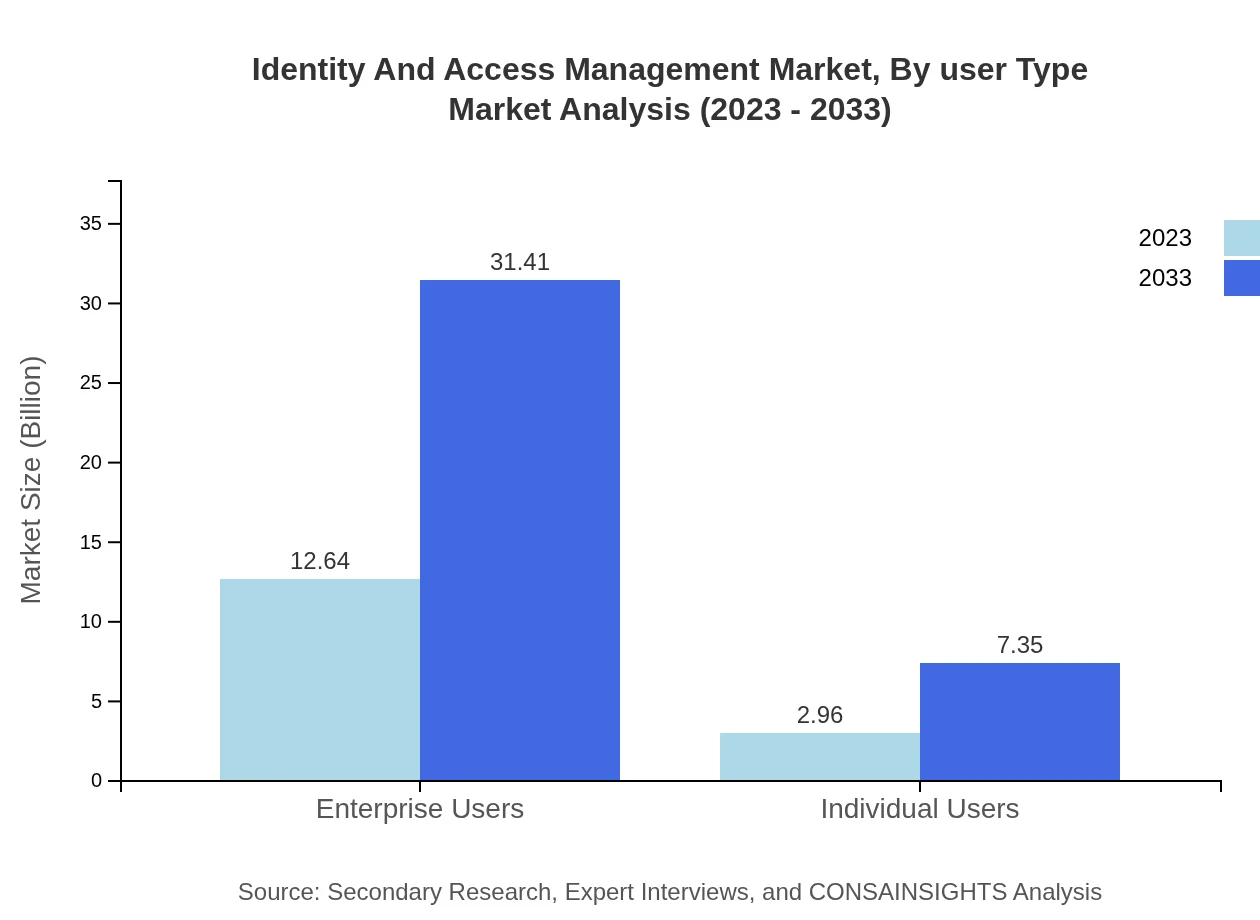
Identity And Access Management Market Analysis By User Type
User types in the IAM market are mainly categorized into enterprise and individual users. The enterprise user segment exhibits considerable growth potential, increasing from $12.64 billion to $31.41 billion by 2033, reflecting the growing importance of secure identity access in business operations.
Identity And Access Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Identity And Access Management Industry
IBM Corporation:
A leading player in the IAM space, IBM offers solutions that integrate advanced analytics and AI to enhance security and user experience.Okta, Inc.:
Renowned for its cloud-based IAM solutions, Okta facilitates secure access and identity management across organizations.Microsoft Corporation:
Microsoft provides comprehensive IAM solutions that leverage its cloud infrastructure, enabling secure access and identity management for enterprises.SailPoint Technologies:
SailPoint specializes in identity governance solutions that help organizations manage identity risks effectively.Ping Identity Corporation:
Ping Identity offers intelligent identity solutions that enhance customer engagement and secure access to applications.We're grateful to work with incredible clients.








FAQs
What is the market size of identity And Access Management?
The Identity and Access Management (IAM) market is projected to grow from $15.6 billion in 2023 to an estimated $40.67 billion by 2033, with a compound annual growth rate (CAGR) of 9.2%.
What are the key market players or companies in this identity And Access Management industry?
Key players in the IAM industry include Microsoft, IBM, Oracle, Cisco Systems, and Okta, which are recognized for their comprehensive IAM solutions and significant market share within the sector.
What are the primary factors driving the growth in the identity And Access Management industry?
The growth of the IAM industry is driven by factors such as increased cyber threats, regulatory compliance demands, heightened focus on data privacy, and the need for secure remote access solutions amidst growing cloud adoption.
Which region is the fastest Growing in the identity And Access Management?
The fastest-growing region in the IAM market is North America, projected to grow from $5.81 billion in 2023 to $14.43 billion by 2033, followed by Europe and Asia-Pacific with significant growth rates.
Does ConsaInsights provide customized market report data for the identity And Access Management industry?
Yes, ConsaInsights offers customized market report data for the IAM industry, allowing clients to tailor their research needs and obtain specific insights based on their operational requirements and market interests.
What deliverables can I expect from this identity And Access Management market research project?
The IAM market research project provides comprehensive deliverables including market size forecasts, competitive analysis, regional insights, consumer trends, and a detailed examination of key segments within the industry.
What are the market trends of identity And Access Management?
Market trends in the IAM industry include the growing adoption of biometric authentication, increased use of Multi-Factor Authentication (MFA), and a rising preference for cloud-based IAM solutions driven by their scalability and cost-effectiveness.