5g Security Market Report
Published Date: 31 January 2026 | Report Code: 5g-security
5g Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the 5G Security market, covering market trends, size, segmentation, and forecasts for the years 2023 to 2033. Insights into technology advancements and regional performance are also included.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
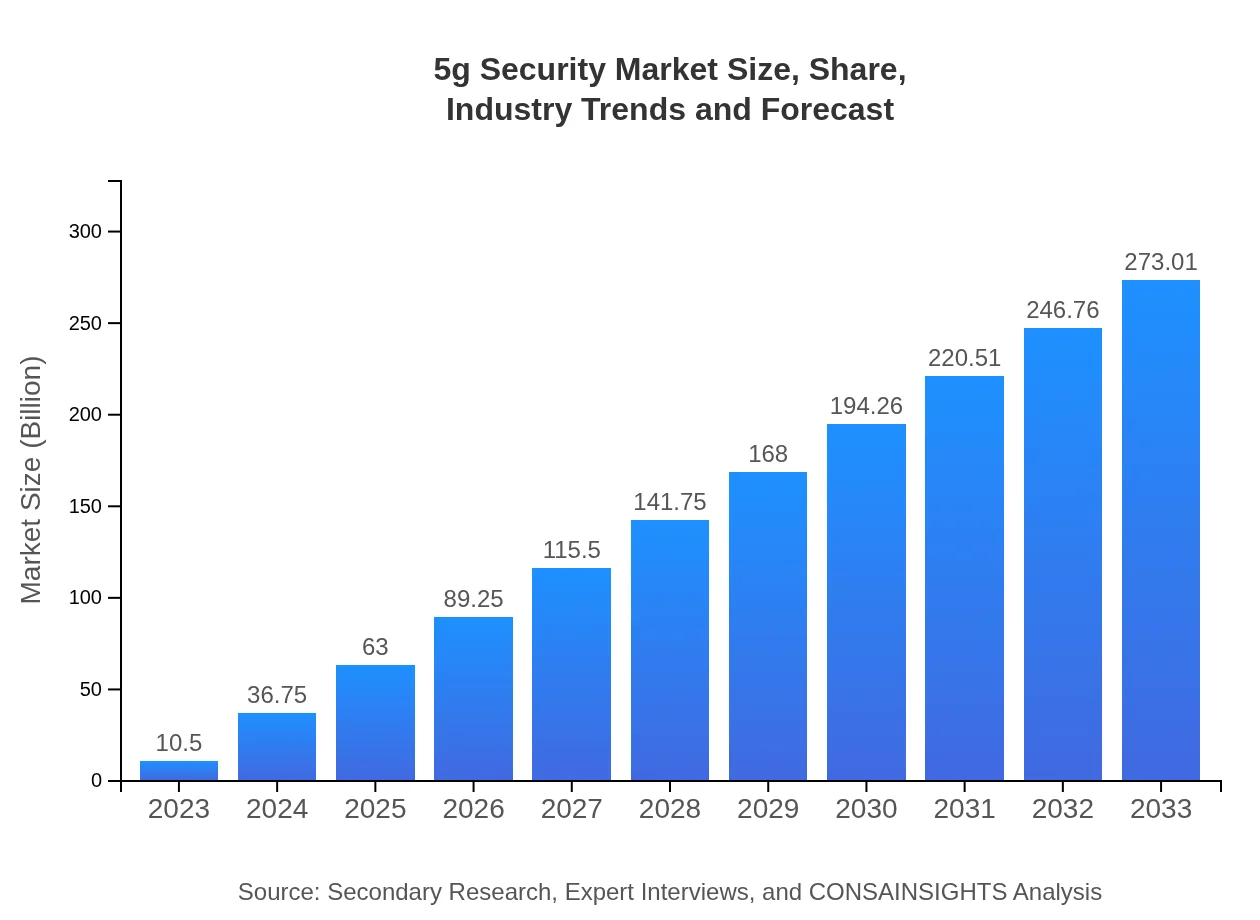
| 2023 Market Size | $10.50 Billion |
| CAGR (2023-2033) | 35.6% |
| 2033 Market Size | $273.01 Billion |
| Top Companies | Cisco Systems, Palo Alto Networks, Checkpoint Software Technologies, Nokia , Huawei |
| Last Modified Date | 31 January 2026 |
5g Security Market Overview
Customize 5g Security Market Report market research report
- ✔ Get in-depth analysis of 5g Security market size, growth, and forecasts.
- ✔ Understand 5g Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in 5g Security
What is the Market Size & CAGR of 5g Security market in 2023?
5g Security Industry Analysis
5g Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
5g Security Market Analysis Report by Region
Europe 5g Security Market Report:
The European market for 5G Security is anticipated to grow substantially, from $3.27 billion in 2023 to $85.10 billion by 2033. European countries are prioritizing cybersecurity amidst stringent regulatory frameworks and increasing cyber threats. The EU's strategic focus on protecting critical infrastructure and enhancing data privacy has fostered an environment ripe for investment in innovative security solutions tailored for 5G networks.Asia Pacific 5g Security Market Report:
The Asia Pacific region is witnessing a significant upswing in the 5G Security market, with projections increasing from $1.92 billion in 2023 to $49.80 billion by 2033. Fast-growing economies such as China, India, and Japan are leading in the adoption of 5G technologies, contributing to an aggressive push for security solutions tailored for verticals like telecommunications and automotive. These countries are investing heavily in 5G infrastructure, presenting vast opportunities for security providers.North America 5g Security Market Report:
North America remains a significant player in the 5G Security market, with the market size expected to surge from $3.75 billion in 2023 to $97.49 billion by 2033. The region is home to some of the largest telecommunications providers who are keen to adopt robust security measures to safeguard networks. Additionally, advancements in IoT and smart city initiatives are propelling the need for sophisticated security solutions as users increasingly rely on digital services.South America 5g Security Market Report:
In South America, the 5G Security market is expected to grow from $0.93 billion in 2023 to $24.11 billion by 2033. Although the market is at a nascent stage, increasing government initiatives and investments in telecommunications infrastructure are paving the way for enhanced security measures. The gradual transition towards digitalization among businesses further underscores the growing demand for comprehensive security solutions.Middle East & Africa 5g Security Market Report:
The 5G Security market in the Middle East and Africa is poised for growth, expanding from $0.64 billion in 2023 to $16.52 billion by 2033. Investments in telecommunications are powering the deployment of 5G technology across urban centers. Nations like the UAE and South Africa are becoming forefront players in adopting 5G solutions, creating a high demand for security systems capable of protecting diverse applications from cyber threats.Tell us your focus area and get a customized research report.
5g Security Market Analysis By Technology
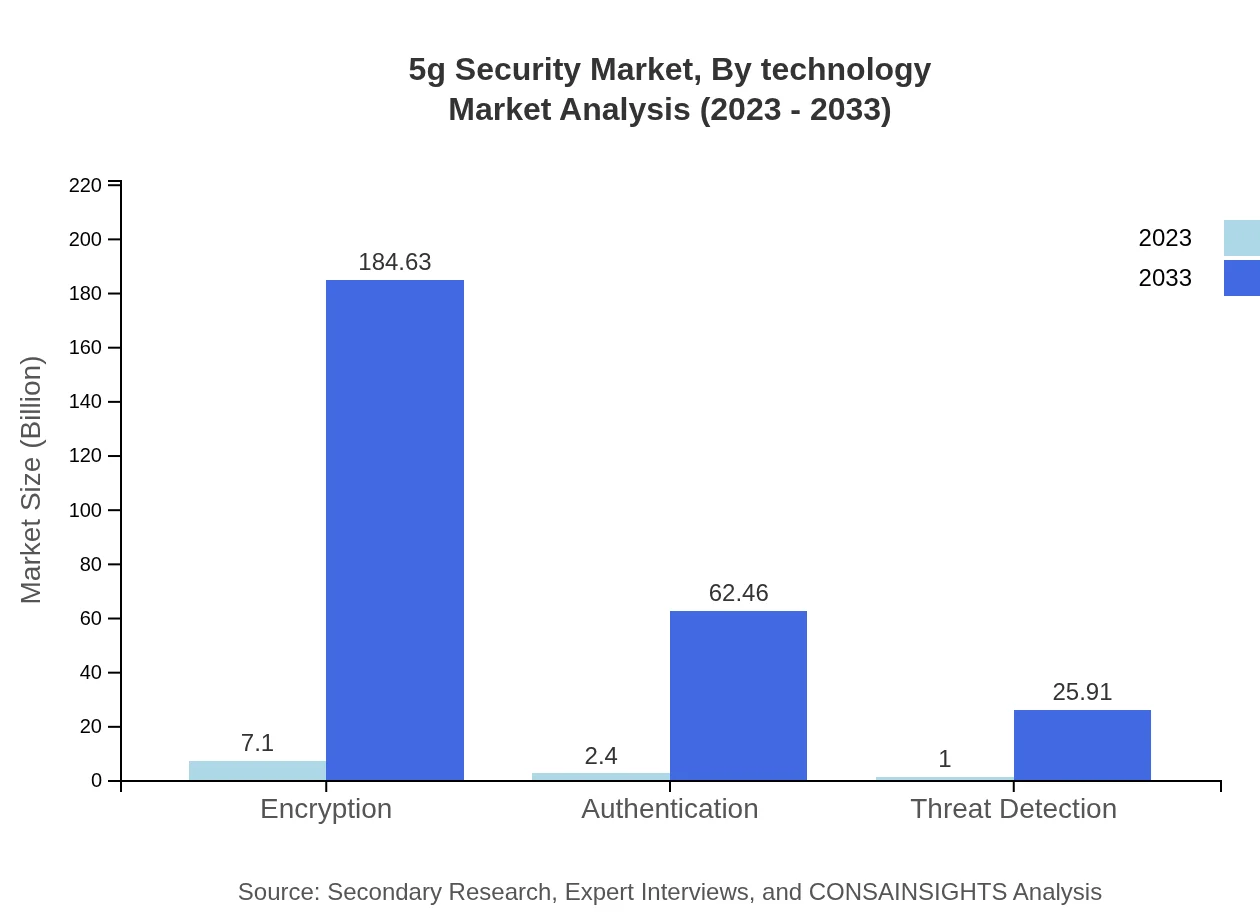
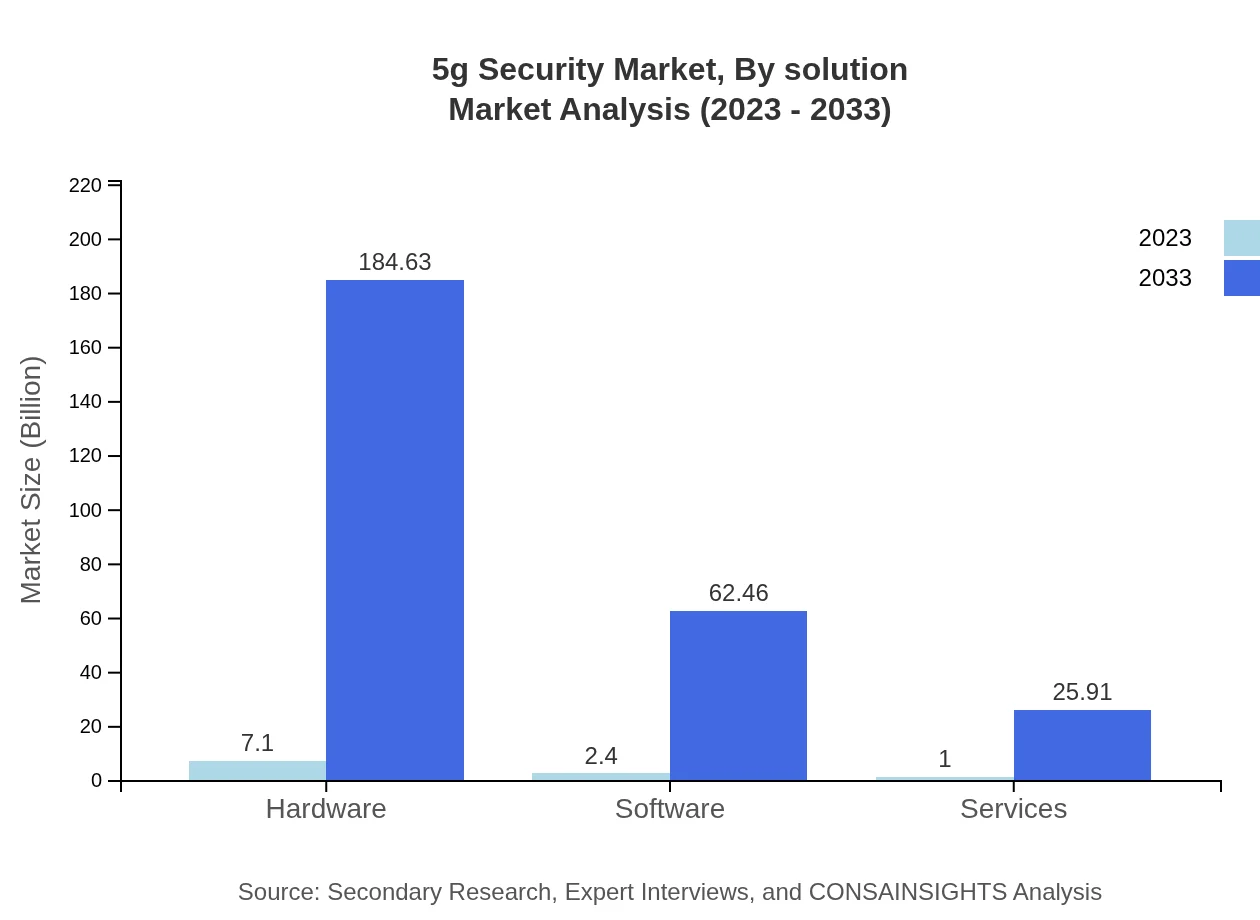
The technology segment of the 5G Security market is categorized into hardware and software categories, with a major focus on IoT Security, Encryption, and Authentication technologies. In 2023, the hardware segment constitutes a notable share, valued at approximately $7.10 billion, and is projected to reach $184.63 billion by 2033. Meanwhile, the software segment recorded an estimated value of $2.40 billion in the same year, with projected growth to $62.46 billion by 2033.
5g Security Market Analysis By End User
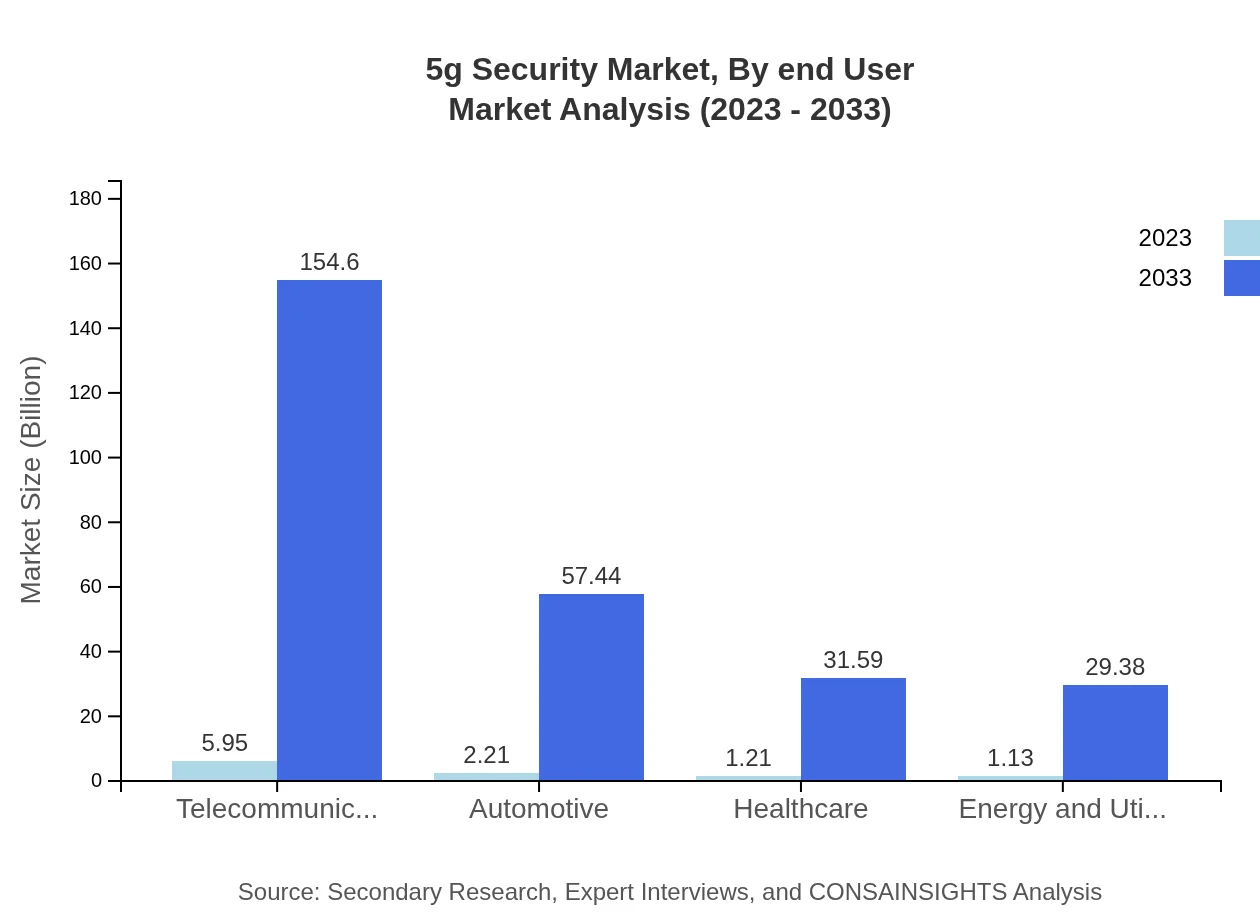
Telecommunications, automotive, healthcare, and energy sectors are the primary end-user industries of the 5G Security market. The telecommunications sector is projected to dominate the market, witnessing substantial growth from $5.95 billion in 2023 to $154.60 billion by 2033. Automotive security solutions are projected to grow from $2.21 billion, reflecting expanding reliance on connected vehicles, reaching $57.44 billion by 2033.
5g Security Market Analysis By Solution
Solutions deployed in the 5G Security market include Encryption, Authentication, Threat Detection, and Data Protection. Encryption is expected to hold a significant market share, with growth from $7.10 billion to $184.63 billion by 2033. Authentication solutions will also witness growth from $2.40 billion to $62.46 billion, responding to the need for heightened security verification in 5G applications.
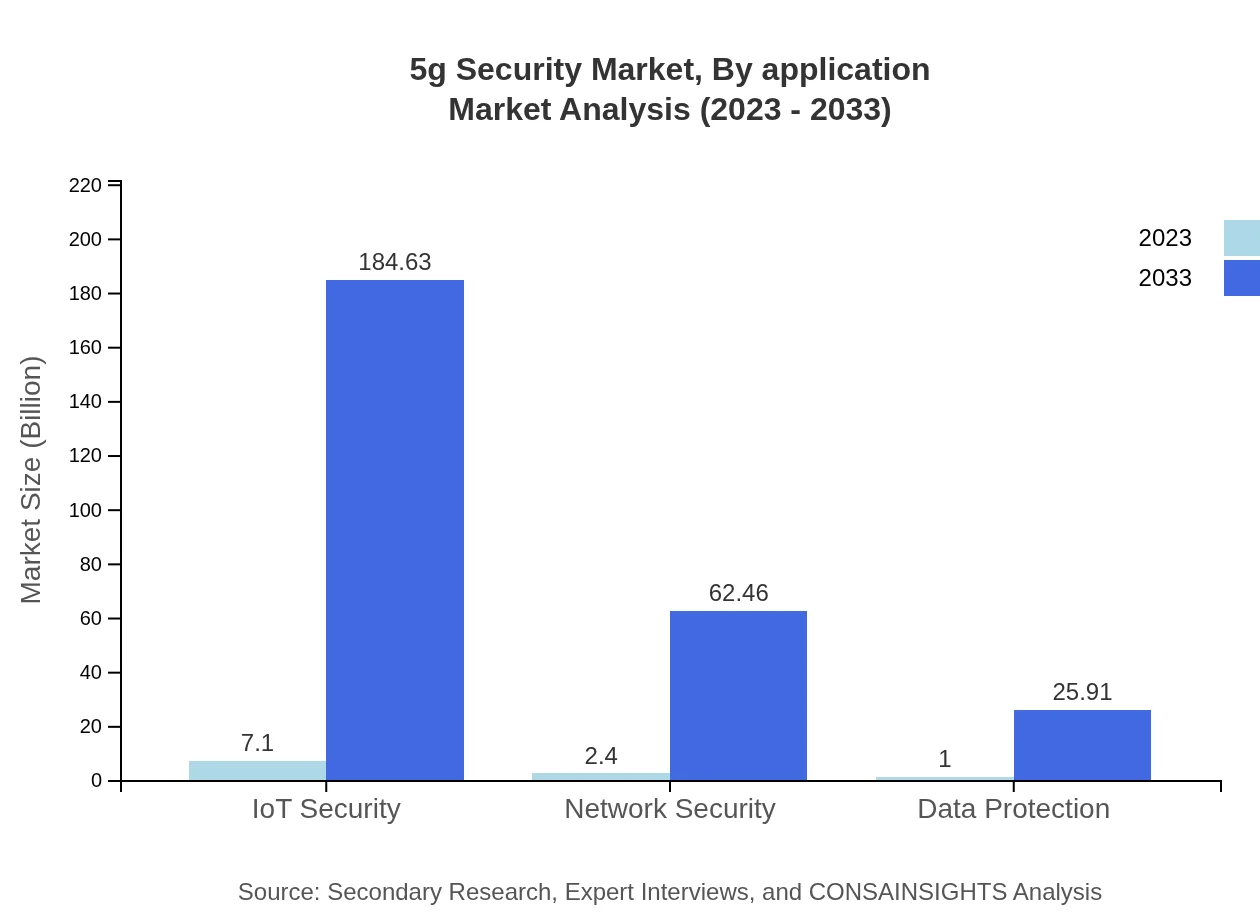
5g Security Market Analysis By Application
Applications such as IoT Security, Network Security, and Cloud Security are influencing the market dynamics. IoT Security stands out with a projected increase from $7.10 billion to $184.63 billion by 2033. Network Security solutions are expected to grow from $2.40 billion to $62.46 billion as enterprises look to secure networks vulnerable to diverse threats.
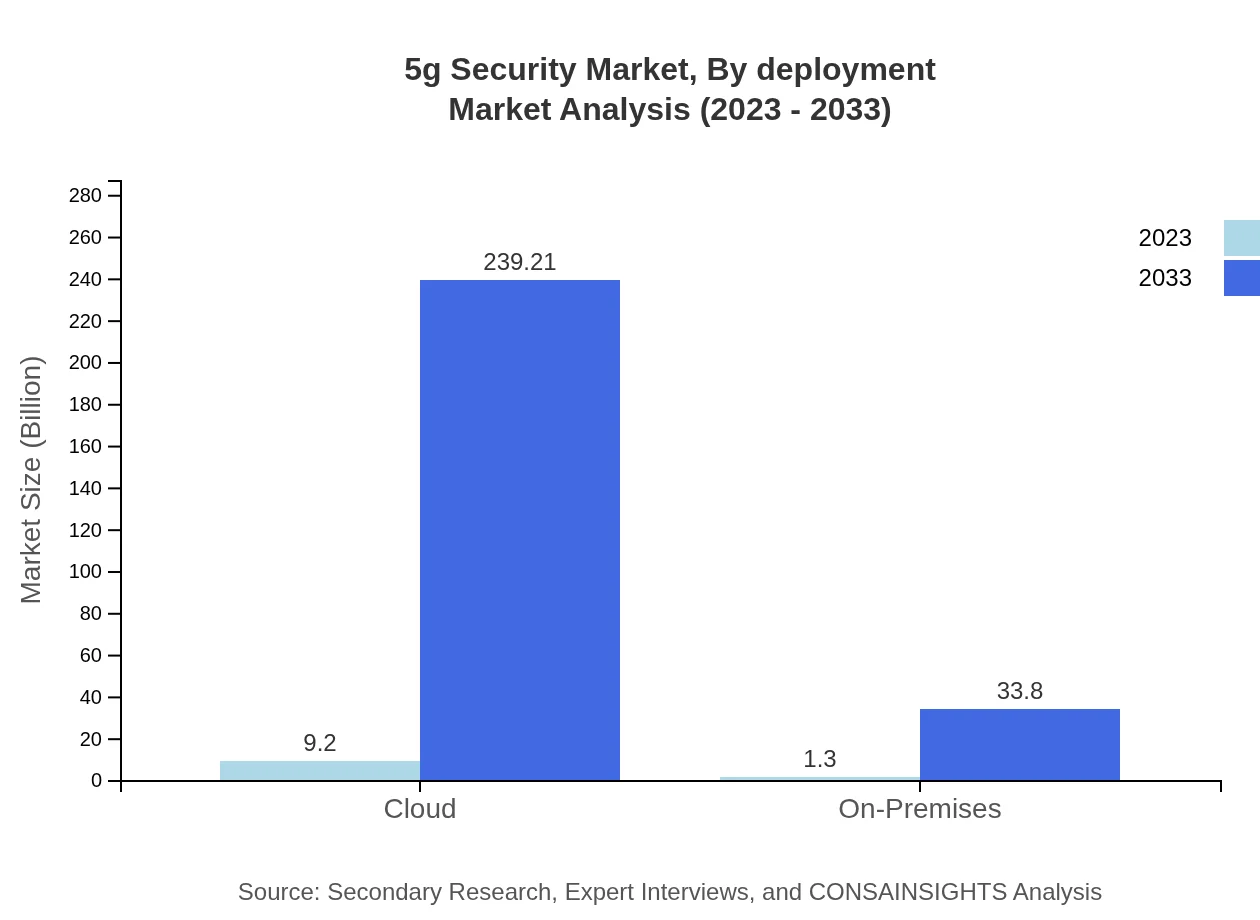
5g Security Market Analysis By Deployment
The 5G Security market can also be divided into Cloud and On-premises deployment models. Cloud-based security solutions are projected to grow from $9.20 billion to over $239.21 billion by 2033, largely favored for their scalability and cost-effectiveness. Conversely, On-premises solutions will also see significant growth from $1.30 billion to $33.80 billion, appealing to organizations prioritizing data control.
5g Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in 5g Security Industry
Cisco Systems:
Cisco is a global leader in networking and cybersecurity solutions, providing a wide array of security products designed for safeguarding data and applications on 5G networks.Palo Alto Networks:
Palo Alto Networks is recognized for its innovative platform that integrates network security solutions, focusing on preventing cyber threats in real-time for 5G deployments.Checkpoint Software Technologies:
Checkpoint offers a comprehensive suite of cybersecurity products to secure software-defined networks and infrastructures, addressing new challenges introduced by 5G.Nokia :
Nokia contributes significantly through its end-to-end security management solutions that ensure the integrity and privacy of 5G traffic.Huawei :
Huawei is a leading global vendor offering a wide range of security products and services to help telecom operators and enterprises enhance their 5G security posture.We're grateful to work with incredible clients.








FAQs
What is the market size of 5g Security?
The global market size for 5G security is projected to grow from $10.5 billion in 2023 to significant levels by 2033, at a remarkable CAGR of 35.6%. This growth underscores the increasing demand for secure 5G networks across various sectors.
What are the key market players or companies in the 5g Security industry?
Key players in the 5G security market include prominent technology companies specializing in telecommunications, cybersecurity solutions, and network infrastructure. Notable firms like Cisco, IBM, and Nokia play pivotal roles in shaping and advancing security measures within 5G networks.
What are the primary factors driving the growth in the 5g Security industry?
The growth in the 5G security industry is primarily driven by the increasing adoption of 5G technology, heightened cybersecurity threats, and the need for robust security measures to protect sensitive data within highly interconnected networks across various sectors.
Which region is the fastest Growing in the 5g Security?
North America is the fastest-growing region in the 5G security landscape, with a market size projected to expand from $3.75 billion in 2023 to $97.49 billion by 2033. Europe and Asia Pacific also experience significant growth in this sector.
Does ConsaInsights provide customized market report data for the 5g Security industry?
Yes, ConsaInsights offers tailored market report data for the 5G security industry, catering to specific client requirements. This includes segmented data analysis, competitive landscapes, and trend forecasts to assist businesses in strategic decision-making.
What deliverables can I expect from this 5g Security market research project?
Deliverables from the 5G security market research project typically include comprehensive market reports, segmented analysis, competitive assessments, trend overviews, and strategic insights, all designed to inform stakeholders and aid strategic planning.
What are the market trends of 5g Security?
Current trends in the 5G security market include the growing focus on artificial intelligence for security automation, increased collaboration between telecoms and cybersecurity firms, and the advancement of security protocols to ensure safe access to 5G networks.