Counter Cyber Terrorism Market Report
Published Date: 31 January 2026 | Report Code: counter-cyber-terrorism
Counter Cyber Terrorism Market Size, Share, Industry Trends and Forecast to 2033
This report provides comprehensive insights into the Counter Cyber Terrorism market, encompassing analysis from 2023 to 2033. Key aspects include market size, growth trends, segmentation, regional insights, technology advancements, and competitive landscape.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
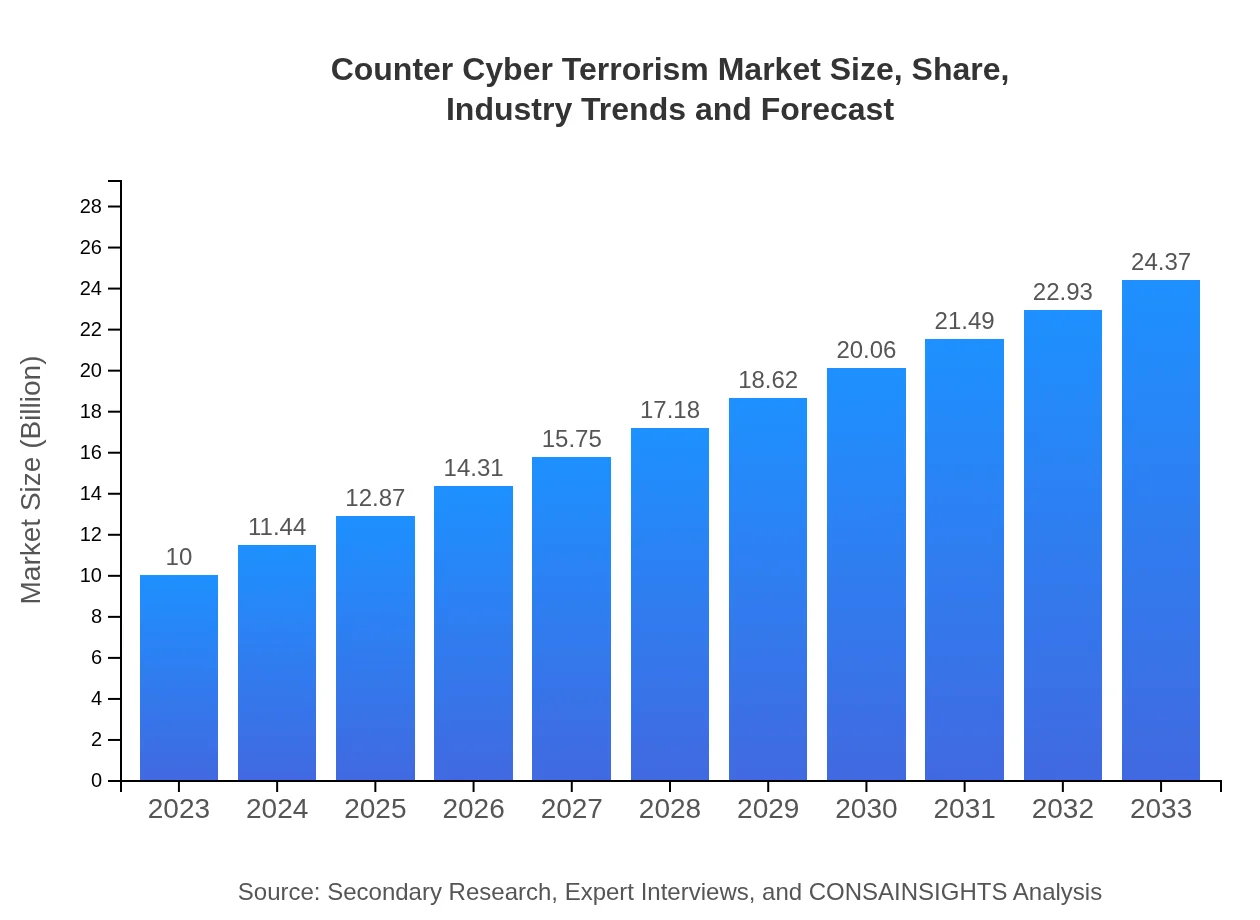
| 2023 Market Size | $10.00 Billion |
| CAGR (2023-2033) | 9% |
| 2033 Market Size | $24.37 Billion |
| Top Companies | Cisco Systems, Inc., Palo Alto Networks, McAfee Corp., FireEye, Inc. |
| Last Modified Date | 31 January 2026 |
Counter Cyber Terrorism Market Overview
Customize Counter Cyber Terrorism Market Report market research report
- ✔ Get in-depth analysis of Counter Cyber Terrorism market size, growth, and forecasts.
- ✔ Understand Counter Cyber Terrorism's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Counter Cyber Terrorism
What is the Market Size & CAGR of Counter Cyber Terrorism market in 2033?
Counter Cyber Terrorism Industry Analysis
Counter Cyber Terrorism Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Counter Cyber Terrorism Market Analysis Report by Region
Europe Counter Cyber Terrorism Market Report:
In Europe, the market was estimated at $2.49 billion in 2023, anticipated to rise to $6.06 billion by 2033. The region's proactive stance on cybersecurity through legislative measures and cooperative efforts enhances growth opportunities.Asia Pacific Counter Cyber Terrorism Market Report:
In 2023, the Asia Pacific Counter Cyber Terrorism market is valued at $2.06 billion, and it is projected to grow to $5.01 billion by 2033. Factors driving this growth include increased government spending on cybersecurity initiatives and rising awareness regarding cyber threats among businesses.North America Counter Cyber Terrorism Market Report:
North America dominates the Counter Cyber Terrorism market, with a valuation of $3.85 billion in 2023 and expected growth to $9.38 billion by 2033. This is largely due to the presence of major cybersecurity firms, increased government funding, and stringent regulations.South America Counter Cyber Terrorism Market Report:
The South American Counter Cyber Terrorism market was valued at approximately $0.44 billion in 2023, and it is expected to reach $1.08 billion by 2033. Growing cyber threats in the region are prompting organizations to invest in more effective cybersecurity solutions.Middle East & Africa Counter Cyber Terrorism Market Report:
The Counter Cyber Terrorism market in the Middle East and Africa began at $1.17 billion in 2023 and is projected to reach $2.84 billion by 2033. This growth is due to the mounting cyber threats facing the region and the increasing vulnerability of digital infrastructure.Tell us your focus area and get a customized research report.
Counter Cyber Terrorism Market Analysis Consulting_services
Global Counter-Cyber-Terrorism Market, By Technology Market Analysis (2023 - 2033)
Consulting Services for Counter Cyber Terrorism are projected to grow from $6.21 billion in 2023 to $15.13 billion by 2033, representing significant market share due to the importance of expert guidance in implementing cybersecurity measures.
Counter Cyber Terrorism Market Analysis Training_and_awareness
Global Counter-Cyber-Terrorism Market, By Solution Type Market Analysis (2023 - 2033)
Training and Awareness programs are forecasted to expand from $2.27 billion in 2023 to $5.54 billion in 2033. These programs are critical for enhancing the cybersecurity knowledge of personnel across various industries.
Counter Cyber Terrorism Market Analysis Support_and_maintenance
Global Counter-Cyber-Terrorism Market, By Industry Market Analysis (2023 - 2033)
Support and Maintenance services are essential, growing from $1.51 billion in 2023 to $3.69 billion by 2033. This growth reflects the ongoing need for upkeeping cybersecurity systems in the wake of evolving threats.
Counter Cyber Terrorism Market Analysis Government
Global Counter-Cyber-Terrorism Market, By Deployment Mode Market Analysis (2023 - 2033)
The Government segment holds critical importance, expanding from $4.79 billion in 2023 to $11.67 billion in 2033, driven by heightened security measures and legislative requirements regarding cyber threats.
Counter Cyber Terrorism Market Analysis Financial_services
Global Counter-Cyber-Terrorism Market, By Service Market Analysis (2023 - 2033)
The Financial Services sector contributes significantly, with growth from $2.15 billion in 2023 to $5.24 billion in 2033. The increasing incidence of cyber-attacks on financial institutions necessitates robust cybersecurity solutions.
Counter Cyber Terrorism Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Counter Cyber Terrorism Industry
Cisco Systems, Inc.:
A leader in networking technology and cybersecurity solutions, Cisco provides various services to mitigate cyber threats in different sectors.Palo Alto Networks:
A prominent cybersecurity firm specializing in advanced firewalls and cloud-security solutions, well-known for preventing cyber threats.McAfee Corp.:
Offers comprehensive cybersecurity solutions including endpoint security and threat intelligence aimed at combatting cyber terrorism.FireEye, Inc.:
Focuses on threat detection and response technology, helping organizations manage complex cybersecurity challenges.We're grateful to work with incredible clients.








FAQs
What is the market size of counter Cyber Terrorism?
The counter-cyber-terrorism market is projected to grow from $10 billion in 2023 to substantial figures by 2033, with a CAGR of 9%. This growth underlines the increasing emphasis on cybersecurity measures globally.
What are the key market players or companies in this counter Cyber Terrorism industry?
Key players in the counter-cyber-terrorism industry include cybersecurity firms, consulting agencies, and tech giants focusing on security solutions. They play critical roles in shaping strategies against cyber-terrorism through innovative technologies and expert guidance.
What are the primary factors driving the growth in the counter Cyber Terrorism industry?
Growth in the counter-cyber-terrorism industry is driven by the increasing frequency of cyber threats, the rising investment in cybersecurity, advancements in technology, and greater awareness among organizations for adopting robust protection measures.
Which region is the fastest Growing in the counter Cyber Terrorism?
North America currently leads with a market size of $3.85 billion in 2023, expected to rise to $9.38 billion by 2033. Europe and Asia-Pacific are also significant, showcasing rapid growth alongside heightened cybersecurity initiatives.
Does ConsaInsights provide customized market report data for the counter Cyber Terrorism industry?
Yes, ConsaInsights offers customized market report data tailored to the specific needs of clients in the counter-cyber-terrorism sector, helping them navigate unique challenges and opportunities effectively.
What deliverables can I expect from this counter Cyber Terrorism market research project?
Deliverables include comprehensive market analysis, segmented breakdowns, trends in cybersecurity, and strategic insights. Reports provide actionable intelligence to aid decision-making for stakeholders in the counter-cyber-terrorism industry.
What are the market trends of counter Cyber Terrorism?
Key trends include increased adoption of cloud-based security solutions, higher demand for consulting services, and emphasis on preventive cybersecurity measures, reflecting a proactive approach to combat potential cyber threats.