Crowdsourced Security Market Report
Published Date: 31 January 2026 | Report Code: crowdsourced-security
Crowdsourced Security Market Size, Share, Industry Trends and Forecast to 2033
This report analyzes the Crowdsourced Security market, detailing market dynamics, size, growth forecasts (2023-2033), and regional insights. It offers valuable perspectives on industry trends, segmentation, key players, and future projections.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
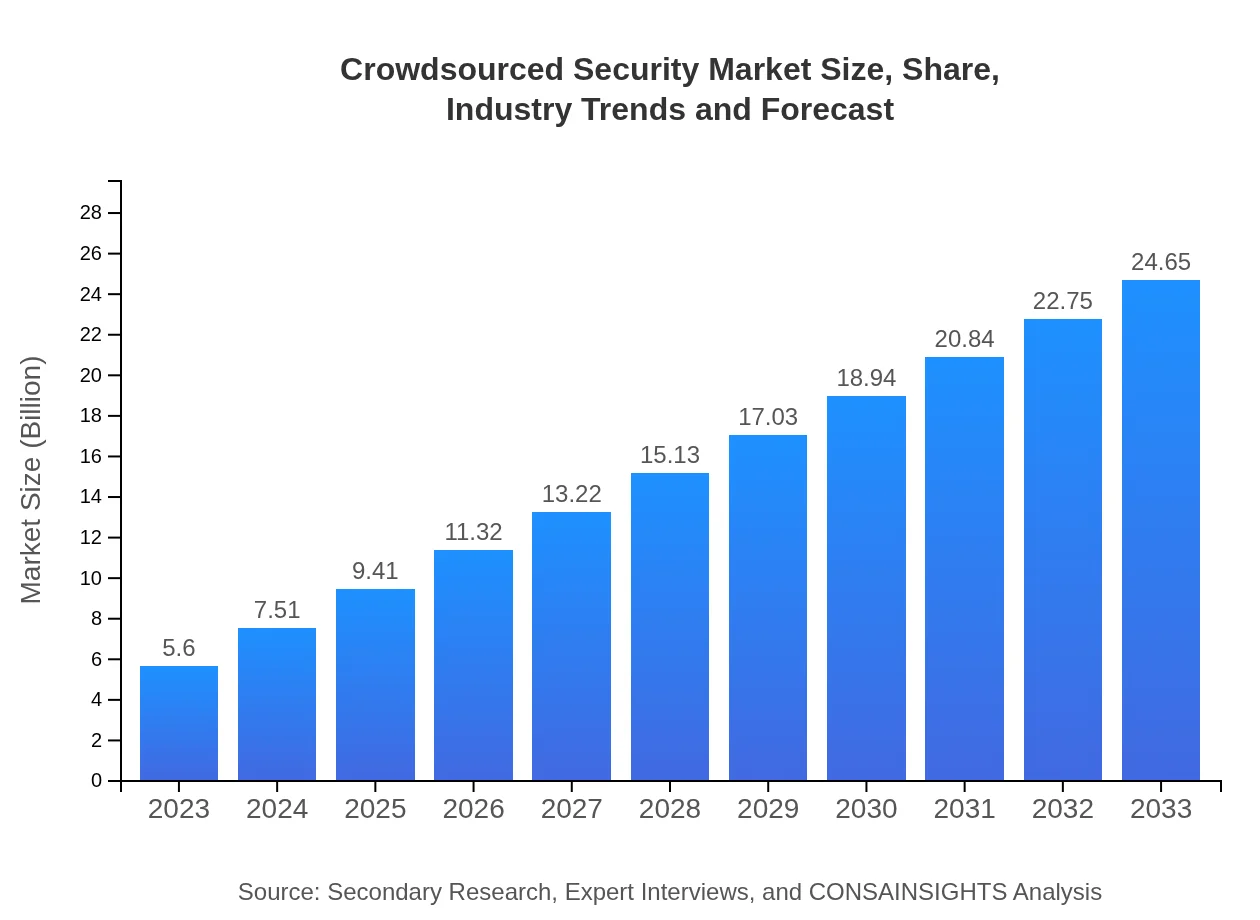
| 2023 Market Size | $5.60 Billion |
| CAGR (2023-2033) | 15.2% |
| 2033 Market Size | $24.65 Billion |
| Top Companies | HackerOne, Bugcrowd, Cymatic |
| Last Modified Date | 31 January 2026 |
Crowdsourced Security Market Overview
Customize Crowdsourced Security Market Report market research report
- ✔ Get in-depth analysis of Crowdsourced Security market size, growth, and forecasts.
- ✔ Understand Crowdsourced Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Crowdsourced Security
What is the Market Size & CAGR of Crowdsourced Security market in 2023?
Crowdsourced Security Industry Analysis
Crowdsourced Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Crowdsourced Security Market Analysis Report by Region
Europe Crowdsourced Security Market Report:
In Europe, the market will grow significantly from $1.70 billion in 2023 to $7.48 billion in 2033, driven by stringent regulations, the need for enhanced security frameworks, and increased adoption of cybersecurity solutions across various sectors.Asia Pacific Crowdsourced Security Market Report:
The Asia Pacific region is expected to experience significant growth, with the market size increasing from $1.06 billion in 2023 to $4.68 billion by 2033. This surge is supported by growing investments in technology and increasing concern over cybersecurity threats among enterprises.North America Crowdsourced Security Market Report:
North America currently leads the Crowdsourced Security market, projected to rise from $2.00 billion in 2023 to $8.82 billion by 2033. The region's advanced infrastructure, increasing regulations, and awareness of cybersecurity are key drivers of market expansion.South America Crowdsourced Security Market Report:
In South America, the Crowdsourced Security market is projected to grow from $0.07 billion in 2023 to $0.30 billion by 2033. The rise in digital transactions and adoption of cloud-based services are expected to bolster demand for crowdsourced security solutions.Middle East & Africa Crowdsourced Security Market Report:
The Middle East and Africa market is anticipated to grow from $0.77 billion in 2023 to $3.38 billion by 2033. Rising digitization, increased mobile connectivity, and awareness of cybersecurity are catalyzing market growth in this region.Tell us your focus area and get a customized research report.
Crowdsourced Security Market Analysis By Industry
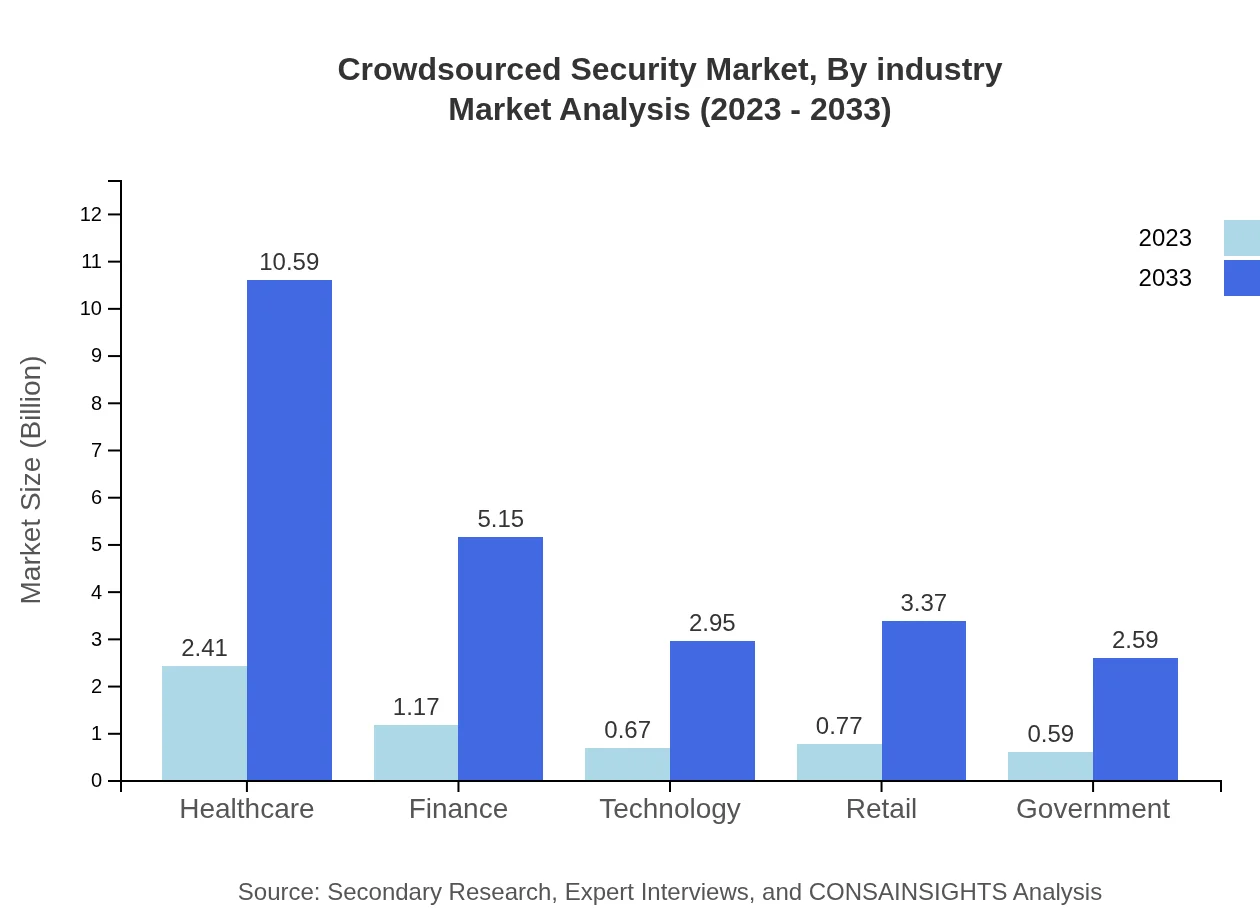
The healthcare sector stands out, with market size projected to grow from $2.41 billion in 2023 to $10.59 billion by 2033, driven by the need for stringent data protection standards. Finance also sees significant growth from $1.17 billion to $5.15 billion in the same period, reflecting the sector’s sensitivity to security breaches. The technology sector grows from $0.67 billion to $2.95 billion while retail and government sectors also experience considerable demand for advanced security solutions.
Crowdsourced Security Market Analysis By Service Type
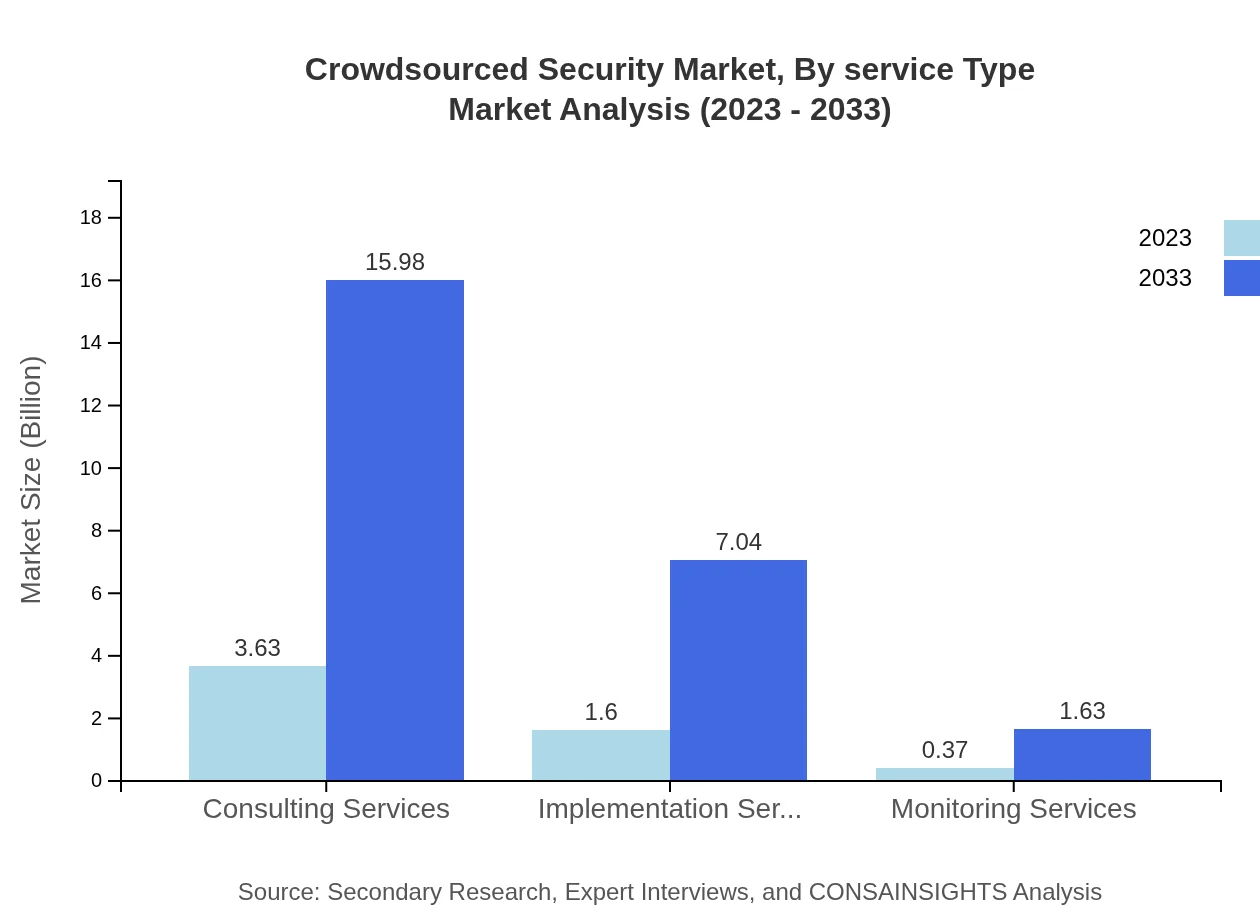
Consulting services remain the largest segment, expected to escalate from $3.63 billion to $15.98 billion by 2033, emphasizing the need for expert guidance in implementing security measures. Implementation and monitoring services also show remarkable growth, from $1.60 billion to $7.04 billion and from $0.37 billion to $1.63 billion, respectively.
Crowdsourced Security Market Analysis By Company Size
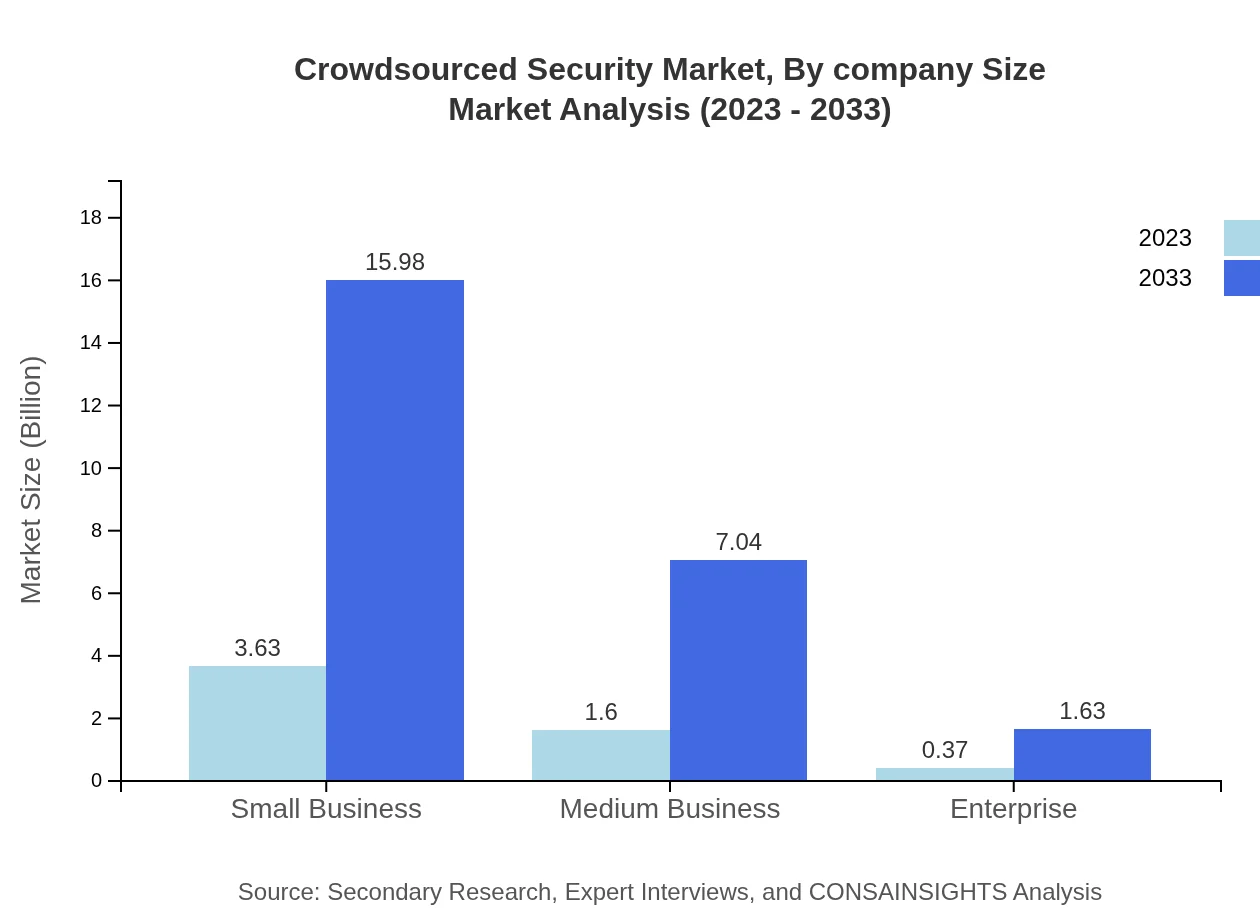
Small businesses make up a significant portion of the market, with size enlarging from $3.63 billion to $15.98 billion by 2033, driven by cost-effective security solutions. Medium businesses will grow from $1.60 billion to $7.04 billion, while enterprise-level organizations see modest growth from $0.37 billion to $1.63 billion, reflecting differing needs and approaches to cybersecurity.
Crowdsourced Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Crowdsourced Security Industry
HackerOne:
HackerOne is a leading platform connecting businesses with ethical hackers to identify vulnerabilities through bug bounty programs, enhancing security across sectors.Bugcrowd:
Bugcrowd offers a crowdsourced security platform focused on comprehensive vulnerability disclosure and penetration testing, helping organizations effectively address security threats.Cymatic:
Cymatic provides automated insights for crowdsourced security testing and vulnerability assessments, assisting clients in proactively managing security risks.We're grateful to work with incredible clients.








FAQs
What is the market size of crowdsourced Security?
The global crowdsourced security market is valued at $5.6 billion in 2023, with a projected growth rate of 15.2% CAGR. By 2033, the market could significantly increase, reflecting the growing demand for innovative security solutions.
What are the key market players or companies in this crowdsourced Security industry?
Key players in the crowdsourced security market include HackerOne, Bugcrowd, Synack, and Cobalt. These companies lead in providing bug bounty programs, vulnerability disclosure, and penetration testing services.
What are the primary factors driving the growth in the crowdsourced Security industry?
Growth in the crowdsourced security industry is driven by rising cyber threats, increased awareness of security vulnerabilities, demand for innovative testing methods, and the growing trend of remote work.
Which region is the fastest Growing in the crowdsourced Security?
The fastest-growing region in the crowdsourced security market is Europe, projected to expand from $1.70 billion in 2023 to $7.48 billion by 2033. North America also shows strong growth opportunities.
Does ConsaInsights provide customized market report data for the crowdsourced Security industry?
Yes, ConsaInsights offers customized market report data for the crowdsourced security industry, enabling clients to receive tailored insights that address specific business challenges and strategic needs.
What deliverables can I expect from this crowdsourced Security market research project?
Deliverables from the crowdsourced security market research project may include comprehensive reports, in-depth analyses, market trends, competitive landscape evaluations, and tailored recommendations for stakeholders.
What are the market trends of crowdsourced Security?
Key trends in the crowdsourced security market include increased adoption of bug bounty programs, a rise in collaboration between companies and ethical hackers, and a focus on proactive security measures to mitigate risks.